FISA, Blanket Searches, and the 4th Amendment
The government has your cell phone and credit card records. What can they do with that information?
So, the NSA has copies of everyone’s phone records. And probably our credit card transactions, too. And goodness knows what else, since it’s all secret. As noted yesterday, I’m queasy but not outraged. While I share Doug Mataconis’s fears about the impact on our liberty, I tend to agree with Michael Reynolds that the actual impact is negligible for reasons laid out at the first link.
Given that I can easily see the national security benefit to a sophisticated data mining operation—which strike me as a lot more tangible than the much-more-intrusive screening process to which we’re subjected every time we fly—and that the sheer mass scale of the operation would seem to preclude snooping on individual citizens unless some pattern triggers a closer look, it strikes me as a reasonable intrusion. The problem, alas, is that this is all conjecture since we really don’t know what the government is doing with the information.
One issue that’s been brought up several times in discussions since this latest news broke is that, since the government has this information, they can now use it in ways unrelated to counterterrorism. Can they now use this for criminal investigations? To enforce the tax code? To blackmail political enemies.
The last of these, surely, would be illegal. I don’t know the law well enough to offer more than conjecture on the first two.
Typically, the government needs to demonstrate probable cause to a judge or magistrate in order to get a warrant to conduct searches. FISA bypasses that process, allowing a “special” court to offer blanket warrants without probable cause on the individual level. It’s legal. Congress has authorized this through various pieces of legislation and the courts are understandably reluctant to overturn the people’s elected representatives on matters of national security, particularly when all the justifications are backed by highly classified materials.
Again, I’m disposed to cautious approval of FISA searches for FISA purposes. But can information obtained this way, bypassing the protections required for traditional searches, then be brought in to traditional cases? If so, that would indeed be a worrisome erosion of Americans’ civil liberties.
The primary remedy in criminal and civil cases for evidence obtained in violation of the 4th Amendment is the Exclusionary Rule. Unique as far as I know to the American system (the Brits think it’s crazy), such evidence is simply not admissible in court. Further, the corollary Fruit of the Poisonous Tree Doctrine also excludes information that the authorities collect pursuant to the unlawfully obtained evidence that they likely found only because of that evidence.*
It seems obvious to me that mass data obtained by the government through the FISA process should be off limits for use outside the national security realm. It’s one thing to use it for leads in breaking up planning for terrorist operations. Or even to start an investigation that leads to a criminal case against people for planning terrorist operations, although that gets murkier. But, surely, it shouldn’t be available to the IRS or the FBI in trolling for information about non-terrorism matters or as leverage in their investigations. If, for example, the government discovered that a citizen was having an extramarital affair through these records and threatened to expose that information if said citizen didn’t cooperate, it would be outrageous.
Moreover, it’s safe to assume that this program will never end. Congress and the American people seem fine with it and it’s inconceivable than an American president will ever decide to give up information that’s potentially valuable for protecting the national security. But, if the information is freely available within the government, then the FBI or IRS would never again need to demonstrate probable cause to get people’s phone and credit card records.
Surely, though, that’s not the case? Surely, the information is available only to the NSA and other intelligence agencies for the requested purpose of data mining? Surely, as with other Top Secret information, it’s not treated as if it were stored in a public library and available to anyone with a valid card but rather available only to those who have the equivalent of a Need to Know for the purposes of the classifying program?
UPDATE: Stewart Baker, former general counsel of the NSA, answered most of my questions in a superb piece for Foreign Policy yesterday.
No one has repealed the laws that prohibit the National Security Agency (NSA) from targeting Americans unless it has probable cause to believe that they are spies or terrorists. So under the law, the NSA remains prohibited from collecting information on Americans.
On top of that, national security law also requires that the government “minimize” its collection and use of information about Americans — a requirement that has spawned elaborate rules that strictly limit what the agency can do with information it has already collected. Thus, one effect of “post-collection minimization” is that the NSA may find itself prohibited from looking at or using data that it has lawfully collected.
I would not be surprised to discover that minimization is the key to this peculiarly two-party, three-branch “scandal.” That is, while the order calls for the collection of an enormous amount of data, much of it probably cannot actually be searched or used except under heavy restrictions. (If I’m right, the administration is likely to find itself forced quite quickly to start talking about minimization, perhaps in considerable detail.)
Even Baker is admittedly forced into conjecture. That’s the nature of dealing with highly classified projects. Indeed:
I have not been briefed on this program. (If I had, I wouldn’t be writing about it.)
But it’s safe to say that this program has been pretty highly vetted by serious people who take the Constitution seriously. Does that preclude abuses? Nope. But this isn’t tyranny run amok, either.
UPDATE 2: Baker adds more reassurance, quoting Director of National Intelligence James Clapper, over at Volokh:
Here’s the DNI:
- By order of the FISC, the Government is prohibited from indiscriminately sifting through the telephony metadata acquired under the program. All information that is acquired under this program is subject to strict, court-imposed restrictions on review and handling. The court only allows the data to be queried when there is a reasonable suspicion, based on specific facts, that the particular basis for the query is associated with a foreign terrorist organization. Only specially cleared counterterrorism personnel specifically trained in the Court-approved procedures may even access the records.
- All information that is acquired under this order is subject to strict restrictions on handling and is overseen by the Department of Justice and the FISA Court. Only a very small fraction of the records are ever reviewed because the vast majority of the data is not responsive to any terrorism-related query.
In short, there’s less difference between this “collection first” program and the usual law enforcement data search than first meets the eye. In the standard law enforcement search, the government establishes the relevance of its inquiry and is then allowed to collect the data. In the new collection-first model, the government collects the data and then must establish the relevance of each inquiry before it’s allowed to conduct a search.
If you trust the government to follow the rules, both models end up in much the same place. I realize that some folks simply will not trust the government to follow those rules, but it’s hard to imagine a system with more checks and restrictions and doublechecks than one that includes all three branches and both parties looking over NSA’s shoulder.
I don’t fully trust the government or any large institution. There’s always the possibility of a J. Edgar Hoover emerging, much less a low level employee misusing the information. At the same time, I trust Clapper and Chuck Hagel and, yes, President Obama as much as one can reasonably trust government officials. (For that matter, I trusted Bush, Cheney, Rumsfeld and company in the same regard–there were abuses in their zeal for going after suspected terrorists but they weren’t using the information to go after political enemies or the rights of ordinary citizens.)
___________
*At least, this was the state of the law in the late 1980s when I last studied it closely.






Yet very few people seem to get upset when asked to submit to sifting though their bodily waist to see if they are doing illegal drugs.
This seems to me to be a “reap what you sow” situation. Clinton wanted to pass a version of the Patriot act in the wake of Oklahoma City, Republicans defeated it. In the wake of 9/11 Republicans passed a version of the Patriot act and them set up FISA Courts over the objections of Democrats who were called terrorist collaborators and such. Republicans have fanned the flames of anti-government mistrust for years and now are in a bit of a pickle WRT support for meta-data mining. I have two points to make here.
1) This partisan mistrust of “Big Government” it a bunch of crap. The party out of power is always anti-government and the in party supports the government (the exact same dynamic plays out with other issues like deficits). Until we break free of the pattern of 14 year old “so’s your old man” bickering for nothing more then cheap political point we are doomed to be lead around by the nose by ill informed populist opinion. All large entities have corrupt elements, big Labor, big business, you name it. If it’s big then at a minimum 20% is corrupt (even organized crime is at least 20% legit).
2) where is the outcry to repeal Patriot act and them set up FISA Courts from either party? Right now there is an effort to make this an “Obama” scandal which it’s not. We as a country clearly wanted this, we voted for it and both of the losing candidates over the last 2 presidential elections, McCain and Romney, would be doing the same damn thing right now if they were in the WH.
So where is the call to repeal these secretive, shadowy, and ill defined laws? I mean for god sake the House has repealed Obama care more times then I can count. Why not spin their wheels at least once passing a repeal of the Patriot act and FISA? My congressman, Mike Rodgers (R-MI) has been in the papers defending the law. Where are the people who dress up in tri-cornered hats threatening to primary him?
As Scott Lemieux says,
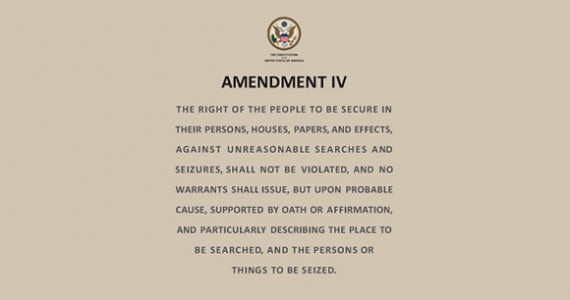
“If the Fourth Amendment still existed one might think that this kind of suspicionless search would pose serious constitutional problems.”
And Rick is right, the problem is the laws that have been passed, not whoever the present resident of the WH is.
All of this acquiring of data is done in the name of making us more secure but is it really suitable to that task? Not being able to identify apparent Lone Wolves like Nidal Hasan is one thing. Not being able to identify active conspiracies, like the Boston Marathon Bombing, is another. The argument would be made, presumably, that the data are necessary but not sufficient.
What is sufficient? If no amount of data would be sufficient is acquiring that much data even necessary? Are they just gathering data in the hope that someday they might have the tools to make it useful? Is that an acceptable purpose? Sheer volume of data might be a barrier to its effective use.
Assurances that anything they sweep up in their search for usable information are nice but IMO it’s a reasonable assumption that if it can be misused then, ultimately, it will be misused. Just as there’s no perfect protection against terrorism, there’s no perfect protection against the misuse of information.
And then there’s the niggling suspicion that all of this, whether orchestrated by the Bush Administration or the Obama Administration, is far more about political security than about national security. As me auld mither used to say “It’s easier to ask for forgiveness than permission.”
The scandal is what’s legal rather than what’s illegal. Clearly, the Congress is complicit in all of this even though they’re now denying they ever intended anything of the scope of what’s actually happened.
That might be comforting if I weren’t convinced that whichever candidate I voted for in the next election would do the same thing.
@Dave Schuler: Yeah. Sensenbrenner is now shocked to discover that there’s gambling in the casino he built.
The news media have lost their minds! It seems to be all about sensationalism! Putting out ALL the facts don’t matter. Let’s just have one hell of a bomb throwing headline. It’s pathetic.
You sounds like someone trying to persuade yourself.
Keep in mind that, just this week, SCOTUS decided that a routine arrest was sufficient to acquire your DNA and use it to look for any other crimes you may have committed. The idea that this massive database will not be used for other purposes — as almost ALL Patriot Act Powers have — is wishful thinking.
As usual the Info Marketplace, there is no longer a news media in USA, is using misinformation and sensational headlines to make it seem that the government is about to take our freedoms that the founding fathers wanted to protect. For one the founding fathers had no idea about electronic technology and they would all agree that it was the POTUS’ job to keep us safe by whatever means necessary. Those leaking secret national security info should be prosecuted as traitors since such disclosures aid our enemies. The info marketplace just wants to get readers and viewers and sadly do not give a hoot about the security of citizens and our country. Finally, congressional reps and senators knew of these programs and it should be their jobs to inform those they represent of governmental programs that affect them in some way. All these reps failed those who voted for them. Voters can now correct this by throwing them out at the next election.
@Hal 10000:
No, my point is that I simply don’t know. I presume that there’s black letter law on this in the open source and am hoping that people will know the answer.
Story goes, Edgar Hoover used to have freshman Congressmen up to his office and gently inform them that a staffer/family member/close associate had red or pink connections. Hoover would look them in the eye and assure them that none of this information would be made public, as the Congressman was undoubtably a loyal American. It wasn’t necessary to go further than that.
Hoover had few problems getting FBI budgets approved.
Would that constitute “blackmail”? If you knew that someone had dirt on your or yours, would you advocate positions that would anger that person?
As to “access” – if information is there, “black letter law” won’t prevent an ambitious individual from finding and using it (especially if encouraged by very senior higher-ups).
Scott McNeally’s “Privacy is dead, get over it” was not a hallelujah. It was an acceptance of powers beyond his control.
I see no reason to frame that rolling tragedy thus:
I doubt Michael does either. No, if you have any kind of hope the only correct politics on this would be a drive for US privacy restrictions. Otherwise you “get over it” and recognize the costs in a networked world.
@James Joyner:
I presume your presumption is correct.
I also presume that it those-in-the-know will not be able to cut through the dross on this issue. If they assure us of the program’s benevolence, a lot of people will just refuse to believe it.
This will become “drones killing American citizens” all over again, a bunch of hyperbole and “civil libertarian” nonsense.
Everyone hates the surveillance state. And we keep on hating it even as we’re watching the Tsarnaev brothers rounding the corners with backpacks slung over their shoulders…
It won’t be. Studies have repeatedly shown that when a law enforcement is granted expanded powers in the name of fighting terrorism, they will end up using it predominately for the investigation of ordinary crimes. For example, less than one percent of the “sneak-and-peek” warrants issued under the PATRIOT act have been used for terrorism investigation. The overwhelming majority have be used for drug investigations.
@James Joyner:
“I have no idea what the truth is, so I will conveniently assume the situation that justifies my apathy.”
@James Pearce (Formerly Known as Herb):
I think it’s foolish to talk about “this program” when each program is just a progression in an overall trend.
The trend, basically, is that people who can afford petabyte databases fill them not with original artwork and compositions, but with “tracking.”
Shall we just pretend there are letters that take that Yahoo data off-limits for government purchasers? That seems a bad assumption. I know government cannot collect that information, but Yahoo has legally done the work for them. Now they only need buy the result.
@James Joyner: It’s been black letter law for a long time that they can’t tap your phone without a court order. I remember seeing a picture of the “FBI room” in, I think it was a New York AT&T building. A room that gave them access in the 50s and 60s to physically wiretap any phone they wanted without bothering AT&T with a warrant . The “penalty” for illegal wiretapping is that they can’t use the resulting evidence in court. However they can use the evidence they just happen to stumble across once they know where to look. Yes, poisonous fruit and all that, but the defense has to be able to prove that.
Law or no law, in the absence of an effective enforcement mechanism, it seems prudent to assume the worst.
I fail to see why I should find it more disconcerting that the NSA is getting access to all this phone and credit card data than that Verizon, Google and Citibank are collecting and storing all this data to begin with. As flimsy as it may be, the NSA has to go through FISA to get access to that data at least, while these companies can use this data however they wish simply by virtue of having a phone service or using credit.
@Scott F.:
When each collector of information only has a narrow set it is less a panopticon.
It is the interchange of data that creates powerful records of an individual. I believe there have been some small steps in privacy legislation to stem that tide, but I don’t think they’ve been terribly effective.
Are you sure that the government has to go through FISA for commercial meta-data?
They can build a heck of a panopticon with what is out there and not proscribed.
James, on your update, do you see that the PRISM contracts negate any restriction on “collecting” for that data set?
@john personna: But I don’t care about the NSA having it any more than I did about Verizon (or, in my case, AT&T) having it. What’s interesting isn’t the collection but what they do with it once collected.
Lots of data collection but only authorized, trained people are allowed constrained access to it, right? RIIIGGHHHTTT, like there’s never been a data breach before ….
@James Joyner:
My position is pretty much a cynical “you have no privacy, get over it.”
To me that’s one of the rational positions. The other is to demand firewalls and limitations.
I don’t really see “no worries, because it’s all OK” making sense. If you move the ball from the NSA and Verizon “having it” to “what they do with it” … so?
You have no guarantees on what they do with commercially purchased metadata.
If no one, even their former general counsel, can tell if they’re actually obeying the law, in what sense is the law a protection? There’s all sorts of laws against law enforcement using criminal databases outside of legitimate investigations, yet they get caught doing it regularly?
http://www.google.com/search?q=police+illegal+access+database
Does anyone really believe that the NSA isn’t regularly ignoring the law as well and counting on the classification system to prevent it from becoming public knowledge?
I have no doubt that the information will be used for regular law enforcement. Maybe not for a few years, but by the end of the decade we will go from using it for terrorism, to the war on drugs, to cracking down on gun runners, to everything.
And, when the likelihood of being caught for a crime escalates — I’m really curious to see what happens to society. Will we be decriminalizing victimless crimes? Will we finally put a stop to cell phone theft?
But more importantly, if the government is collecting all this information about me, why can’t they just do my f’ing taxes? Put the survellience state to a friendly use.
@Scott F.: You should be set by both.
For me, the issue is not so much what is the law today but what will it be tomorrow?
And, looking at general trends in technology and civilian law enforcement, I’m pretty concerned. Due to costs, among other things, DNA evidence used to be reserved for only “special” cases (and often used as much to exonerate as to capture). We know how that changed earlier this week.
Likewise, we’ve seen a general trend in “military grade” tech making the jump into civilian law enforcement work.
Finally, one needs look no further than recent supreme court cases involving the Fourth Amendment – http://www.theatlantic.com/technology/archive/2013/06/security-state-creep-the-real-nsa-scandal-is-whats-legal/276625/ – to see that the general trend has been towards what could be called a “weakening” of it in the face of emergent technologies.
As I wrote elsewhere, if we accept that these tools “work” and help catch “bad people”, it doesn’t take much to envision them coming home to roost — first applied to the worst of crimes (murder, child porn) and then, slowly, spinning out from there.
@James Joyner:
This.
And on that point, it’s worth thinking about this point that Matt Frost (@mattfrost) brought up last night:
“Nice of the NSA to create a one-stop shop for any foreign service good enough to crack it.”
What are the chances that China or another power might have already accessed part, if not all, of the current data repository?
@Matt Bernius:
What happens though when everyone is a criminal?
http://www.amazon.com/Three-Felonies-Day-Target-Innocent/dp/1594035229
Most of us have broken lots of federal laws without even knowing it. The only reason we’re not all in jail is that we haven’t pissed of a prosecutor or law enforcement officer enough for them to bother figuring out exactly what those laws were. The problem with this technology is that it each new breakthrough makes it easier and easier for the government to use the law to punish people who’s real crime is annoying a government official.
Picking up here where I left off with Spartacus on an earlier thread. I posed the question, why should I be outraged, what practical difference does it make. He was kind enough to answer. I’m going to paraphrase his arguments and hope I do a fair job of it.
I assume this would be a case where data mining shows a person who is suspected of terrorist plotting has also, for example, downloaded kiddie porn. Or perhaps the target of investigation is merely legally raising money for some anti-US group and the government wants him to stop so they say, “You know, we found out that cheerleader porn of yours is of a 14 year-old.”
Fair point. Could happen.
The defense against this is to reply to the government that you are going to continue to speak freely and invite them to fwck off. Just because a state has surveillance it is not by any stretch all-powerful. Let me put it this way: a state does not become totalitarian because it has the physical means. All states have the physical means in the form of armies and police forces. Data mining does not in my opinion lead inevitably to totalitarianism.
In fact, what does sometimes lead to totalitarianism, is fear and desperation. Is it not very likely that Israel’s drift ever further rightward is a consequence of living under fear of terrorism? They way to eliminate fear of terrorism is to eliminate or at least greatly reduce the threat. Which of course is what this program claims to do. When people feel scared or endangered they want a daddy.
I think that’s completely wrong. Privacy/secrecy is what allows child abuse to flourish. As for gay rights the single most important thing in my opinion has been outing of gays, whether voluntary or involuntary. Obliterating that secret as a secret made more straight people face their prejudices and made fewer gay people willing to be passive.
I still fail to achieve outrage over this issue because I look at it in practical, personal terms: do I have a problem with all of you knowing who I called last week? No. Do I have a problem with you knowing my peccadillos? No, so long as I know yours as well. My guess is we’d all about even out on that. Do I care if you know what I spent or what I make? I get asked the “money” question when I do school visits and the teachers always wince, but I just go ahead and answer. I answer because I can’t think of any good reason not to.
Has anyone noticed the series of Wal-Mart commercials that’s running, the purpose of which is to get us to forget what we now know about how Wal-Mart treats its employees? They’re forced to defend themselves publicly against charges they treat people like sh!t. Why? Because privacy was surrendered in favor of letting people know the truth.
Imagine a completely transparent world. You know what I buy, and I know the same about you. You know what ex-girlfriend I looked up on Facebook, and so does she. You know my kinks, I know yours. You see my American Express receipts and I see yours. You know what I had for dinner, and I know the same about you. So what?
Privacy and shame go hand in hand, I think. If you’re not ashamed of what you do then what’s the problem? And isn’t it likely that you’re only ashamed of what you do because you fear exposure before other people who do exactly the same thing but who will hypocritically condemn you and put you at a disadvantage? Is this necessarily the best way to organize society?
@michael reynolds:
Thanks for the response. I’ll try to address your comments to my last two points.
While it’s true that a good defense to the government’s implied suppression of speech is to say “fwck off,” many people won’t do that because they fear govt pressure, public attention, being ostracized by co-workers, risks to their employment, etc. They may have children or spouses that really don’t want the attention. It’s the very reason most of us use pseudonyms when commenting on blogs – anonymity enables us to say things we wouldn’t otherwise say.
Should we toughen up and say what’s on our minds without the benefit of anonymity? It will depend on the cost to be paid, which cannot be known in advance. Either way, the goal of encouraging people to speak freely is undermined by the diminution of privacy.
With respect to greater respect for LGBTs, I agree with you that the outing of gays is a major factor in greater public acceptance. But for those gays who came out voluntarily and were accepted by their acquaintances, I think that acceptance was attributable, in part, to society’s adoption of the concept of personal privacy. Basically, people thought to themselves that another person’s sexual orientation is his/her private business. Without an embedded notion of the concept of personal privacy, many people may not have been willing to accept that another person’s orientation was a private matter.
Having said all that, I understand that even if everyone were to accept all of my arguments “outrage” still may not be the appropriate response from all. After all, the only thing that changed yesterday was that we learned what had been occurring for years. No new harm actually happened yesterday and there are plenty of actual, immediate harms that did occur and do warrant real outrage. So, I guess it depends on one’s personal tolerances. I think I’m saying that even if one isn’t outraged by this, one should still strongly oppose it.
Michael, I think you’re taking far too narrow a view of “practical harm”. What practical harm does offiicial prayer in schools, confiscating all of the copies of a newspaper with an article the government doesn’t approve of, mandatory selling of all firearms to the government, or any other violation of rights that doesn’t cause physical or economic harm do? If your definition of practical harm is narrow enough, none.
The problem is that the violation is harm. They are inherent rights secured by law and when the law fails in securing them that is harm.
In my view blanket warrants are harm. You can take a step beyond that to the potential use that might be made of the information but IMO you don’t need to. Violation of an inalienable right is itself harm.
@Ben Wolf:
I’m not trying to be obtuse here, but why? Why should I be upset about both?
Unlike michael reynolds, I value the right to privacy. What I do behind the closed doors of my house is my family’s business and ours alone, while the same holds true for my bedroom door and my spouse and the clinic door and my doctor, etc. I believe having spaces that are protected from the prying eyes of Big Government and Big Business is a liberty worth having and worth fighting for.
But, I don’t see how meta-data on phone calls, credit card usage or Internet browsing belong in that protected space. Each of these acts is a public one where I leave the protected space of my home albeit virtually. How are these activities any different than walking in a public space and being recorded on a surveillance camera or going to the store and having the clerk observe what I buy?
@Dave Schuler: @Spartacus:
Prayer in schools is forcing someone else’s beliefs on my children, that’s why it’s harm. But yes, I agree that a Constitutional violation — if that’s what we have — is in itself harmful.
I think the difference in our perspectives is that I take the view that privacy — our temporary, time-specific, society-specific, to some extent class-specific notions of privacy — will prove untenable in the world we’ll be inhabiting. In fact they are being broken down by choice: Facebook, Twitter, the various picture services, as well as by our use of Google, credit cards, toll booth transponders, etc…
That’s why I go ahead and use my own name here. It’s why I answer all questions kids put to me. It’s why I’ve decided just to adhere to the truth in my statements unless of course it would be rude or hurtful to do so. I find there’s a great sense of invulnerability in just being who you are.
Google and Apple and American Express and Wells Fargo and the rest already know everything there is to know about my daily activities, interests, etc… My “secrets” are already out there. Does it change anything for me if the NSA also knows those things? Not a bit.
I don’t know whether PRISM is a violation of the 4th Amendment, I imagine the Supremes will weigh in on it eventually. I take the Constitution very seriously. But as a personal matter am I outraged that the NSA may have logged my phone calls? No.
One other point. I agree that we overestimate the direct threat of terrorism. It’s never been the direct threat that bothered me. What bothers me is what effect more terrorism would have on our society. Do I cut the TSA and the NSA slack because I’m worried about being killed by terrorists? Not at all. I cut them slack because I know how panicky and overreactive the people and the pols will be if terrorism recurs. Better an ounce of prevention than the ten pounds of “cure” that would come raining down if there were a second 9/11.
@michael reynolds:
Google et al won’t ever combine that knowledge with, for example, any controversial comments you’ve made on a blog and then feel justified to go knock on your door or your neighbors’ or employer’s doors to investigate whether you’ve committed a crime. And that means that Google et al can’t be the cause of your ostracism or stalled career at the defense contractor you work for.
The feds can and will do all of those things and people will have real difficulties in their lives as a result. Knowing that in advance, many people will choose not to say things that might be considered controversial.
@Spartacus:
I don’t trust Big Business any more than I trust Big Government. No, they can’t arrest you, but they can ruin your credit rating thus massively messing up your life. And pre-Obama they could randomly decide to cancel your health insurance. And do you have any reason to assume Google doesn’t sell data to foreign governments?
@michael reynolds:
I’m not at all supportive of Big Business’ surveillance and data mining efforts. I’m merely arguing that the harm that can come from surveillance and data mining by Big Business is not nearly as great as the harm that can come when govt does it.
And I’m arguing that this overreach by govt weakens other rights we have such as the right to free speech.
Not being as young and spry I used to be, I must sign off now but I appreciate and hope to continue the exchange.
@michael reynolds:
I forgot to post this link, which lays out my concerns better than I can articulate.
http://www.economist.com/blogs/democracyinamerica/2013/06/verizons-records
@Spartacus:
Many of us are not as spry as we used to be. Good night.
@michael reynolds: @Spartacus: A couple years back, Stilgherrian brilliantly described Google as “a data mining company in the United States.”
@Spartacus:
The charge in evidence is that Verizon supplied
That is enough to make a personal travel history for every Verizon wireless customer.
In answer to that we’ve had executives from Google and Facebook saying “we didn’t do anything that crazy.”
It is a gray area how crazy they got, and what if any barriers they perceive. Certainly Google could decide to be as accommodating as Verizion, right?
Again, I don’t see a useful separation between “when business does it” and “when goverment does it.” Verizon did it, and then supplied it.
@john personna: @michael reynolds:
I’m drawing a distinction based on who is the end-user of the data. It seems to me that if you’re arguing that how Big Business uses the data is as bad as how Govt uses it you have to make at least one of the following claims:
1. The govt harm I described won’t/doesn’t actually happen
2. The harm from Big Business’ use of the data is worse than the govt harm (and you’d need to describe the harm from Big Business’ use)
I have yet to hear anyone make either of these claims.
@Spartacus:
OK. As I say, I vote “equal” harm and increasingly “inseparable” data.
I make it a rule not to get upset over the inevitable, starting with my own inevitable death.
Data, once it exists, will be disseminated. We can try to slow that process, but we won’t stop it. I think we are at one of those inflection points, one of those paradigm shifts, to use (and abuse) two much-abused phrases.
I think the 20th century version of privacy is gone and is not coming back. So I ask myself whether that’s such a terrible thing. Does a loss of privacy make it harder or easier for evil to flourish? A case can be made either way, and depends largely on one’s individual fears.
My go-to tool for assessing threats is to awfulize, to imagine the worst and then ask myself whether the worst is really so bad. So, if tomorrow a magic wand were waved and suddenly all personal data on all of us were published, would that be a terrible thing?
I don’t think it would.
Privacy enables hypocrisy. Hypocrisy allows he who has not been exposed to deride he who has. A complete openness would leave very few people in a position to preach. It would force us to face our actions and justify them, not merely assert our morality and crusade on that basis. In other words, he who wished to be seen as moral would actually have to be moral. Based on the last 5,000 years of recorded human history, I doubt the likelihood of a sudden outbreak of genuine morality. Which would mean that we would all be exposed as sinners, to use the religious terminology.
Given, too, that modern communications has the capacity to spread exposed data far and wide, and given the fact that we are naturally more interested in the peccadilloes of public individuals – big shots – the exposure would fall most heavily on people in positions of influence and authority. They would be in a position either of having to live spotless lives or of admitting that they were not quite as high on that pedestal as they might wish us to believe.