Password Strength FAIL
Through 20 years of effort, we've successfully trained everyone to use passwords that are hard for humans to remember but easy for computers to guess.
xkcd illustrates that “Through 20 years of effort, we’ve successfully trained everyone to use passwords that are hard for humans to remember but easy for computers to guess.”
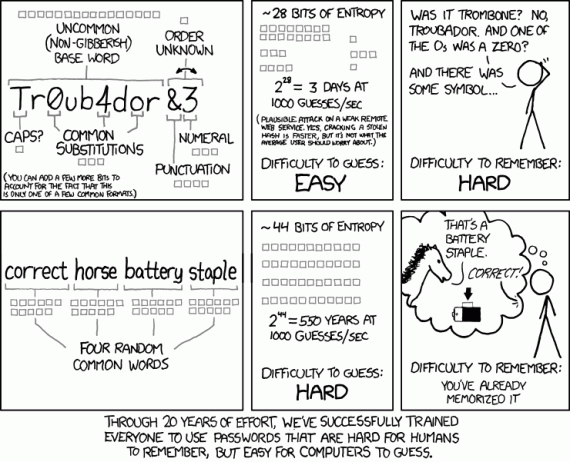




Sort of like the Enigma.
I recently read an article about the same topic. That’s why my new passwords have been something like “YouShouldReadOTBEveryday.”
The sad fact is that the even the “easy to guess for computers” password is a veritable Fort Knox compared to what a large percentage of people actually choose for their passwords.
I heartily recommend that folks click on the link to the original cartoon and let their mouse “hover” over the original cartoon. XKCD always has “mouseover” text that is often more brilliant than the actual cartoon.
J.
Passwords are getting better. It used to be that “password” was the most common password. Now it’s “password1”. Progress!
@Dave Schuler: Thanks HEAPS, Dave. Now I gotta go reset all my passwords…
J.
The four-word password is still not great. Let’s say that there are 5000 common words. Then all four word combinations can be guessed in four years. Throw some parallelism at the problem, such as in the form of GPGPU, etc., and the problem becomes tractable.
Still, this means you are safe from the casual, random hacker, but not safe from the FBI, NSA, etc.
@Anon:
That’s only feasible if you have something like a hash file that you can process offline. If you’re doing the “try different combinations at the login screen”, which is what most users should actually be concerned about, the limiting factor is waiting for the remote authentication to succeed or fail after each attempt.
My son uses a 30 random character password plus thumprint identification. According to some website his password alone would take 49 duodecillion years to break. I can only assume he’s hiding some really good porn.
@Anon: 5000 common words? I seriously doubt that. A quick Googling shows that the OED says there are over 600,000 words in English, and other sources say the average English native speaker has a vocabulary of 10,000 words, and that’s hardly the same 10,000 words across the board. Plus, people would be more inclined to pick “unusual” words that have meaning to them. I enjoy salting my writing with unusual words, and once a reader tried to check me on “codswallop” — but she checked other sources first, and found out what she had always thought was a made-up term is valid. Similarly, when people want to mock Andrew Sullivan, they tend to use “gobsmacked.”
The four special words rule sounds pretty damned good to me. Toss in a creative misspelling or two, and it’s even better. One of my common passwords is a catchphrase nonsense word from high school, with the first letter doubled, and a second double lettter, singled. Another is a song title that is actually a phrase from a foreign language.
J.
@Anon: You’re assuming that the hacker knows that you’re using this template. The working assumption here is that passwords are completely random and are being hacked by brute force. In that case, you’re better off with one with more characters (takes much longer to hack) and that’s easy to remember so you don’t screw yourself.
@Stormy Dragon: is correct. Most systems won’t allow anywhere near 1000 guesses per second, in fact most will lock an account after too many login failures. There are insecure systems, but password cracking is not the easiest way to attack them.
The easiest way to crack a password is the oldest: look for a post-it note with a strange word or character string on it, usually stuck on the bottom of the monitor. Careful users will stick it on the back of their monitor or the bottom of their keyboard.
@James Joyner:
The working assumption of the cartoon is that passwords are excessively non-random, even when a user is making what s/he thinks are “random” changes to a word.
In practice, people trying to “brute force” passwords via an on-line application (web app, SSH server, etc) almost never assume that passwords are random strings. Even folks doing offline attacks may do better trying common passwords first, before resorting to exhaustively testing every possible password (it depends on the hash being attacked, available hardware, and the expected complexity of the passwords).
As for password length: longer is usually better. But, predictable is worse than longer. If you’re just worried about someone guessing your password via on-line guessing, something like “40cfe2” (six random hex digits) is probably less likely to be hacked than longer, but much more common passwords like “trustno1” or “1q2w3e4r”.