Computer Virus Hits Drone Fleet
A computer virus has infected America's fleet of Predator and Reaper drones.
A computer virus has infected America’s fleet of Predator and Reaper drones.
Danger Room’s Noah Schachtman broke the news (“Exclusive: Computer Virus Hits U.S. Drone Fleet“):
A computer virus has infected the cockpits of America’s Predator and Reaper drones, logging pilots’ every keystroke as they remotely fly missions over Afghanistan and other warzones.
The virus, first detected nearly two weeks ago by the military’s Host-Based Security System, has not prevented pilots at Creech Air Force Base in Nevada from flying their missions overseas. Nor have there been any confirmed incidents of classified information being lost or sent to an outside source. But the virus has resisted multiple efforts to remove it from Creech’s computers, network security specialists say. And the infection underscores the ongoing security risks in what has become the U.S. military’s most important weapons system.
“We keep wiping it off, and it keeps coming back,” says a source familiar with the network infection, one of three that told Danger Room about the virus. “We think it’s benign. But we just don’t know.”
Military network security specialists aren’t sure whether the virus and its so-called “keylogger” payload were introduced intentionally or by accident; it may be a common piece of malware that just happened to make its way into these sensitive networks. The specialists don’t know exactly how far the virus has spread. But they’re sure that the infection has hit both classified and unclassified machines at Creech. That raises the possibility, at least, that secret data may have been captured by the keylogger, and then transmitted over the public internet to someone outside the military chain of command.
[…]
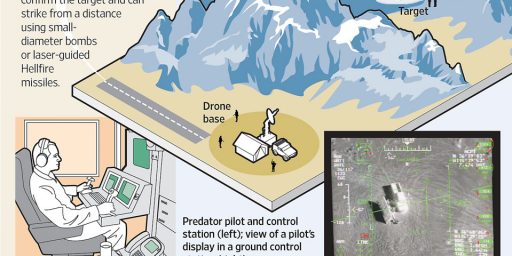
But despite their widespread use, the drone systems are known to have security flaws. Many Reapers and Predators don’t encrypt the video they transmit to American troops on the ground. In the summer of 2009, U.S. forces discovered “days and days and hours and hours” of the drone footage on the laptops of Iraqi insurgents. A $26 piece of software allowed the militants to capture the video.
The Atlantic’s Alexis Madrigal (“This Is Bad: The US Drone Fleet Has Been Infected With a Virus“) wonders, “Even if — and from Shachtman’s reporting, it’s still an if — nothing nasty happens with this virus, what does it say about the state of our security infrastructure that this happened?”
Our own Alex Knapp, writing at Forbes, (“America’s Drones Have Been Infected by a Virus“) has apparently learned the lessons of Battlestar Galactica well: “The more that America’s security capabilities depend on data transmission and computerized weapons, attacks of this nature are inevitable, and computer security should be a significantly high priority. If keylogger software can infect these systems, how long will it be until another program captures more data from UAV surveillance missions? Or worse – enables someone else to take control of the drones?”
Amusingly, Fox News (“U.S. Military Drones Infected With Mysterious Computer Virus“) is trying to take it all down a notch:
It’s not immediately clear whether the virus hit the system intentionally or by accident. But the existence of ordinary-seeming computer viruses on what should be the most extraordinarily secure of military systems is far from shocking, said Anup Ghosh, a former scientist with the Defense Advanced Research Projects Agency (DARPA) and chief scientist with security company Invincea. They’re just computers, after all. “[The drones] are controlled by standard PCs,” Ghosh told FoxNews.com. “None of this should be surprising.” The system should be replaced or “re-imaged” with a virus-free, bit-for-bit copy of the data on the drive in order to get rid of the infection, he said. “If they are connected to a larger network they will be infected again,” he said.
A senior Air Force source with knowledge of the drone program and familiar with the virus that was caught in recent weeks told FoxNews.com that Wired’s story is “blown out of proportion” and “vastly overwritten.” “The planes were never in any jeopardy of ‘going stupid’,” the source said, and the virus “is not affecting operations in any way … it showed up on a Microsoft-based Windows system. We have a closed-loop system and heavily protected cockpits — the planes were never in jeopardy.” The virus was introduced when the Air Force was transferring data maps between systems using external hard drives, he said. Very quickly the Air Force protective network tracked the virus. “The system worked,” the Air Force official said.
Worth keeping an eye on but I’m actually inclined to believe the official disclaimer here absent more evidence.





I sometimes wonder why the military IT personnel insist on using technology in such a direct manner rather than have the info follow numerous different & benign off the radar sites before encrypted info hits their computers. The use of bouncing off different IP’s seems to work so well for the bad guys.
Did Fox mean “Windows, what do you expect?”
Computer folk may remember this blast from the past (1998):
Makes me think of http://xkcd.com/694/
Being Microsoft-free is a very good feeling.
It’s not just a MS issue. Hack a Mac
And don’t even get started on Unix/Linux
@Davebo: Too late, I got started on Linux 7 years ago and haven’t looked back since.
I’ve been saying for a decade now that you an forget the second amendment. If you want to legitimately be armed against government aggression learn to hack/crack/phreak. That’s way more threatening than any number of guns.
The only thing keeping AQ from this kind of thing is they’ve always sucked with technology. Groups like anonymous probably wouldn’t make a real effort to suborn military weapons but might well make a try at sabotaging them as a show of force/joke. The real question is a power like China that has the technical savy and the potential military aims.
Probably because of lag, Sarah.
Every bounce takes time, and any time delay can be a problem when you’re flying (and fighting).
@Michael: I’ve been running the same install of XP for the last 5 or so years and I’ve only had minor problems with viruses/malware. Do keep in mind I’ve exposed this machine to some seriously malicious websites but I’ve been able to keep it clean with a few commonsensical precautions.
I don’t know about the rest of you but I’ve actually been getting more and more macs in lately that are infected with some rather nasty viruses.
@Tlaloc: Anonymous is just a random mashup of people varying from really really skillful people to simple script kiddies that run whatever the skillful people tell them to. I wouldn’t be too terribly worried about them as they aren’t interested in destroying the society they live in.
Personally my first reaction to this was “I wonder if China was involved”. I would be far FAR more worried about China in this circumstance as they have already launched attacked on American sites..
@matt: I’m not overly surprised by the Macs coming in, the user is still the weakest link when it comes to security, and Mac’s suffer from the same “Find something on the internet and install it” mentality as Windows, and that’s how the majority of malware seems to be spread these days.
That’s why I like all my packages signed by the developer. Even when Debian’s archive server was hacked, if the hackers had infected any of the packages they would have failed to install on anybody’s computer. And again when the Linux kernel’s source control server was compromised, we could still be confident that the source wasn’t tainted because it was also signed.
@Michael: Very true and it’s not helped by the people running around claiming Macs are secure and cannot be infected.. It’s good business for me but not good on my client’s pocket books.
@Davebo:
It has been quite a while since the NSA produced a locked down Linux version, as reference. I’m sure it was just a starting point, but it was also pretty much a path not taken. For some reason we didn’t use the fact that the NSA (etc.) could read every inch of open source to produce our secure military systems.
It could be that MS has given some source to the NSA, but it still isn’t as many eyes.
@ponce: Dang that lag time…seems Steve Jobs gave up the ghost before his brilliant mind could figure a way around that vexing issue. I just bet he or some other bright person could/can find a solution because he/they knew/know there are no problems, just solutions. So many intelligent people, so few answers.
@john personna:
On the contrary, SELinux has been integrated into the Linux kernel since 2003. There is also AppArmor, which accomplishes the same thing as SELinux, and is also now a part of the Linux kernel.
@Michael:
I was aware of but did not emphasize the merge. I was really speaking to Davebo’s
and the “might have been” was not about the merge per-se, but about the path that would have been an NSA authored DOD distribution.
(You talk about signing above, I’m thinking the armed forces would like an NSA-signed version.)
I don;t disagree but if this was a common run of the mill virus that has gotten into drone control software and thrived there (as evidenced by the inability to root it out) then it wouldn’t require serious skills to do the same thing intentionally. As I said I don;t see a group like anonymous trying to hijack a weapon to cause real carnage but to prove a point or just for the lols? Yeah I think some of them are capable of trying.