Password Security Waste of Time
Company policies requiring you to constantly change your password? Almost certainly more harmful than useful.
The study, by a top researcher at Microsoft, found that instructions intended to spare us from costly computer attacks often exact a much steeper price in the form of user effort and time expended.
“Most security advice simply offers a poor cost-benefit trade-off to users,” wrote its author, Cormac Herley, a principal researcher for Microsoft Research.
Particularly dubious are the standard rules for creating and protecting website passwords, Herley found. For example, users are admonished to change passwords regularly, but redoing them is not an effective preventive step against online infiltration unless the cyber attacker (or evil colleague) who steals your sign-in sequence waits to employ it until after you’ve switched to a new one, Herley wrote. That’s about as likely as a crook lifting a house key and then waiting until the lock is changed before sticking it in the door.
Herley also looked at the validity of other advice for blocking security threats, including ways to recognize phishing e-mails (phony messages aimed at getting recipients to give up personal information such as credit card numbers) and how to deal with certificate errors, those impossible-to-fathom warning messages. As with passwords, the benefits of these procedures are usually outweighed by what users must do to carry them out, he said.
[…]
He calculated that if the approximately 200 million US adults who go online earned twice the minimum wage, a minute of their time each day equals about $16 billion a year. Therefore, for any security measure to be justified, each minute users are asked to spend on it daily should reduce the harm they are exposed to by $16 billion annually. It’s a high hurdle to clear.
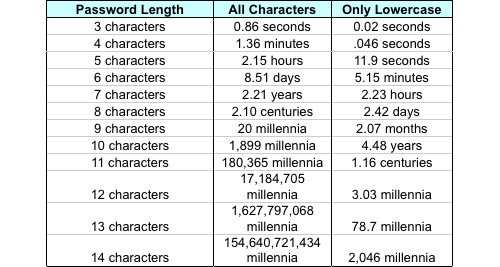
This isn’t to say that all computer security measures are bad, of course. A widely circulated blog post noted, “Adding just one capital letter and one asterisk would change the processing time for an 8 character password from 2.4 days to 2.1 centuries.”
The post also suggests obvious things like not using a loved one’s name or your Social Security number as the base of the password. But, for the most part, the security measures that IT departments force on people are counterproductive.






One question that’s come up to me is whether you should use different passwords to all the different places you visit. It sure would be much easier to remember just one really good password.
I’m just wondering how improbable it is that a password thief would figure out what other sites you visit and what user name you use at those sites, etc. Anybody?
Having worked in secure environemnts previously and being responsible for my company’s data now, allow me to say I disagree strongly. There is no question that good security costs money, but that is a cost of doing business. We implement strong passwords in my company and require them to be changed every 90 days, partly as a good security practice and partly to remain in compliance with existing and anticipated laws requiring us to have policies in place to protect customer data. Sharing or writing down passwords and leaving them where anyone can find them is a firing offense. Good audit trails are essential in my business, and I assume most businesses, and without good authentication you may have no idea who is doing what to which data after the fact. This is almost always a bad thing.
The proposed costs also seem to assume that everyone is being dragged away from otherwise productive activities.
Charles, I have a question. I work for a technology company, and thus, am subject to these damn policies.
If I have to change all my passwords every 90 days, I am eventually going to run out of passwords that I can reasonably remember, particularly if I am required to use different cases and special characters. How in the hell am I supposed to remember all of these constantly changing ridiculously complex passwords, particularly if I can’t write them down???
The answer to Ben’s question is simple:
When required to change your password, simply change it in some insignificant (but memorable) way, such as adding “2” to the end. Then, every 90 days, do it again by changing it to a “3” or a “4”.
Which is what everyone I know does. And which renders the security policy useless. Which it is. Which is exactly Dr. Joyner’s point.
I believe in strong, unique, passwords for production accounts, and weaker, replicated, passwords for less serious “personna” accounts.
I think the automatic timeouts cut both ways though. If they are too short or for less serious accounts they encourage password degradation over time.
Now, if you auto-generate strong passwords every 90 days you’ve got good words, but you are implicitly encouraging note-keeping. But hey, there are fairly secure ways to keep cheat sheets. A password scribbled on the back of a business card in a wallet, without a clue to which server it belongs, is pretty safe.
(You can also scribble passwords knowing that you always write an extra letter at the end, etc. You can use the password, but the low-tech thief who borrows your note probably will not try variations.)
Ben, welcome to the wonderful world of professional adulthood. There are many tasks each of us have that seem silly, timewasting, or just plain nuts, and yet they have to be done to keep the machine humming along. Just because you don’t see the utility doesn’t mean there isn’t one, kind of like most process metrics. Hey, I wish we lived in a world where this wasn’t necessary, but, alas, we don’t.
There are many good techniques for generating meaningful passwords and being able to remember them. At any given time I have over forty passwords that I have to remember. I say that not to brag but just to note that if I can do it, I expect most people can.
charles, that’s a stupid argument. Security is the focus of your job; it’s not the focus of other peoples’ jobs; nor is it likely the main focus of your business and most definitely not most businesses. I can think of plenty of other non-core areas at my job where, if allowed to run rampant over the core money-generating focus, would and could present you with the same difficulties the rest of us have on a regular basis with insane password policies.
Well as an aside, I worked one place where the first day they said “you’re a developer, you’ll need all the root passwords.” I said “I think I’ll like it here.”
We went from zero to a $5 billion dollar company while I knew those words. Then IT staffed up and they said “john can’t have root passwords!”
I shook my head and thought “where were you when we were going from zero to 5 big ones?”
Well, stupid is as stupid does, or something. I’ve seen too many real stories only once removed to not use strong passwords on any business accounts.
Security isn’t my business, but I do have legal obligations to protect the data I have.
Charles, way to a condescending jerk. I’m not new to a professional position, nor to adulthood. What I was saying with my post (and pointed out by others) is that for 95% of employees, you’re either going to get strong passwords that are written down, or you’re going to get trivially incremented ones that aren’t. And that’s it. Because to expect otherwise is naive on the part of IT/Security.
Mr. Austin,
You’ve been providing some reasonable arguments, but you haven’t actually refuted the basis for Herley’s recommendations. I think you can, however:
This $16 billion figure is irritating me. That’s every man, woman and child spending a minute per day on changing passwords. Uh, even if all employed citizens have to change 10 passwords every three months (and it only takes a minute for the slowest user to change a password), this just isn’t adding up to $16 billion. That’s just a magic BS number.
Second, let’s have a few financial firms or the military play loose with security, and suddenly the damages can climb pretty fast. Billions are not out of the question.
Regardless, I’m still curious as a relative layperson if it’s okay to use the same very good password (or a small number of very good passwords) for a number of different accounts. I don’t currently, but I’d like to hear what anybody thinks.
When you use passwords across organizations, you are putting some trust that no one at org “A” will spot your account at org “B” and try your same password.
I say “some trust” because this may not be that easy for the random system administrator at “A”. Good systems secure passwords in things called “one way hashes” which allow the system to confirm your password, without actually knowing what it is. Of course, any admin who is willing to put in the work at “A” can recover your password, one way or another.
(BTW Franklin, if you are looking for more proofs of the argument, shouldn’t you show where losses came specifically from low quality passwords? I’m not aware of that happening in any high profile case. More often passwords are given to 1000 people, 1 of whom turns out to be untrustworthy. A better password doesn’t turn a bad apple good again.)
Charles is correct that a lot of these policies are driven by state and local laws. What is a waste of time however is how they are implemented by an organization. Our password reset policy is vexingly, boneheadedly cumbersome to the user. Also it’s kind of stupid since half the people use Macs which, since they don’t connect the AD environment use local password which are not encumbered by centralized password enforcement make them security breach vectors in a huge way yet this breach is not addressed at all.
Our most sensitive system requires complex passwords changed every 90 days and enforces a uniqueness an absurd uniqueness policy which means they can’t be changed in a trivial way and insures that these passwords are all written down somewhere typically on a piece of paper hidden conveniently under a users keyboard. So i disagree with Charles that these systems are helpful.
The only way, in my opinion, to manage high security environments is with third party solutions that make all of this transparent to the user and use a hardware/single password combo but since the laws don’t require it and it’s $$$ we get the key under the front door mat solution.
There is a strong parallel to the TSA safety system here. TSA, and your local IT department, can add procedures. Some of them improve security, but some just become ritual. The ritual moves become a way to assure people that security is in place. Or at least CYA.
Take off your shoes, change your password, everything will be fine. Never mind that bombs move from shoes to underwear, or that the guy deleting information has a perfectly valid account and password.
(It is critical that companies have good systems in place to quickly remove access for departing employees. And don’t forget accounts with vendors. We had to clean up after a guy who was fired from one of our customers. They forgot to inform us.)
Ben, sorry, didn’t really mean for it to come across as condescending. My apologies.
As to people writing their passwords down, it all starts at the top. If management wants it, provides adequate direction and followup, then passwords won’t be written down. If the fail at any of these, then they are contributing to it being a waste of time.
Some of the commenters seem to be unaware of the theiving that is going on with much greater frequency than they apparently realize online. The criminals are international and very sophisticated.
So how many of those were by brute-force password attack(*), and how many were good passwords obtained by phishing(**), etc?
I think IT emphasizes strong passwords because it is something they can control, not because it is a major cause of loss.
* – For the non-computer types, you can set up one computer to contact another and just try password after password. Fortunately for us most of our accounts are now protected two ways. They force us to wait when we type the wrong password, so that a brute force attack is dragged down to human speed, and cannot test say a million passwords per hour. More importantly, most accounts now have false-try limits. After 10 fails or whatever, the account will be automatically deactivated.)
** – when a user is tricked into giving up their password to a bad party.
Good point. I don’t know of any big cases and couldn’t find them in a quick search. I’m just assuming that a single breach in credit card info could cause quite a few charges to be racked up before it was stopped, which the credit card company or its insurer would end up being responsible for. But yeah, not a billion dollars or anything.