The SolarWinds Attack
Our enemies are getting more brazen and sophisticated in their cyber warfare.

While President Trump continues to sulk over losing his re-election bid, his government is scrambling to deal with the latest cyber attack from Russia and various parties are weighing in to tell us that it is huge and ongoing.
WSJ has an excellent roundup that’s thankfully not paywalled at the moment (“Hack Suggests New Scope, Sophistication for Cyberattacks“):
The suspected Russian hack that compromised parts of the U.S. government was executed with a scope and sophistication that has surprised even veteran security experts and exposed a potentially critical vulnerability in America’s technology infrastructure, according to investigators.
As the probe continues into the massive hack—which cast a nearly invisible net across 18,000 companies and government agencies—security specialists are uncovering new evidence that indicates the operation is part of a broader, previously undetected cyber espionage campaign that may stretch back years.
The attack blended extraordinarily stealthy tradecraft, using cyber tools never before seen in a previous attack, with a strategy that zeroed in on a weak link in the software supply chain that all U.S. businesses and government institutions rely on—an approach security experts have long feared but one that has never been used on U.S. targets in such a concerted way.
They provide this helpful illustration:
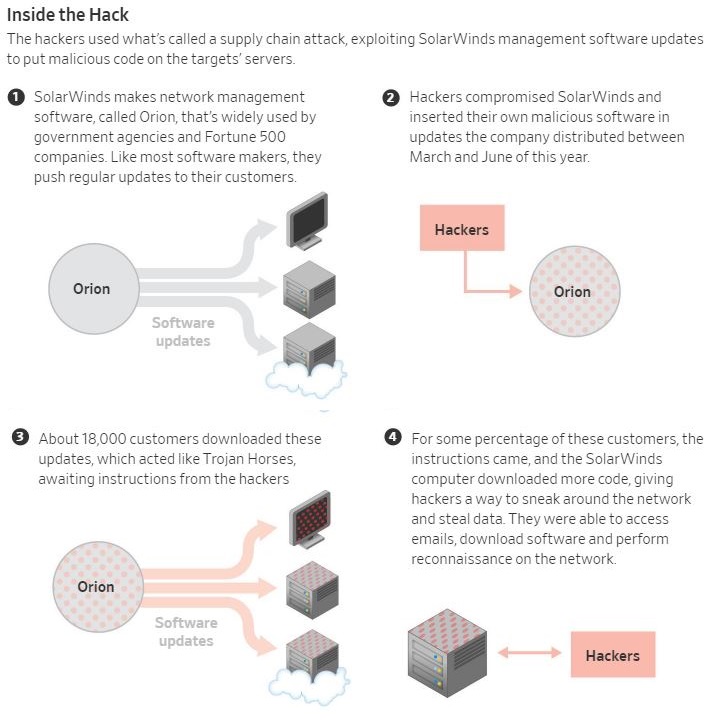
The hackers used the digital equivalent of a spy’s disguise to blend in with the flood of data flowing through government and corporate networks and remain undetected. They snatched up years-old but abandoned internet domains and repurposed them for hacking, and they named their software to mimic legitimate corporate tools. Most devastatingly, they sneaked their malicious code into the legitimate software of a trusted software maker—an Austin-based company called SolarWinds Corp. and its software called Orion.
The Cybersecurity and Infrastructure Security Agency tasked with protecting U.S. networks, in an alert Thursday, said it had evidence that the hackers have managed to break into computer networks using bugs other than the SolarWinds software. The alert labeled the hack a “grave threat” to compromised victims, which it said include multiple government agencies, critical infrastructure entities and private sector companies.
Hours later, the National Security Agency, America’s top cyberspy organization, issued a broader warning to defense agencies and contractors about vulnerabilities such as those exposed by the SolarWinds attack. Hackers, it said, were finding ways to forge computer credentials to gain wider access across networks and steal protected data stored on in-house servers and cloud data centers. The approach, the NSA said, may have been used in an attack on VMware Inc. software used in national security circles that the spy agency warned about earlier this month.
Government officials and cybersecurity experts have concluded that Russia is likely responsible for the hack, in part due to the extreme skill involved as well as other classified clues, according to people familiar with the matter. At least two senators who have received briefings in recent days have openly referred to it as a Russian operation. Moscow has denied responsibility.
Government officials and lawmakers are still working to understand the full consequences of the hack, which is viewed as a classic but highly successful attempt to spy on internal communications and steal information that could be valuable to Moscow’s intelligence agencies. It isn’t considered a destructive attack that damaged or shut down computer systems, as some major cyberattacks have done in the past
Microsoft president Brad Smith has declared the need for a global response, using some rather alarmist language:
This latest cyber-assault is effectively an attack on the United States and its government and other critical institutions, including security firms. It illuminates the ways the cybersecurity landscape continues to evolve and become even more dangerous. As much as anything, this attack provides a moment of reckoning. It requires that we look with clear eyes at the growing threats we face and commit to more effective and collaborative leadership by the government and the tech sector in the United States to spearhead a strong and coordinated global cybersecurity response. [emphases mine throughout-jj]
He joins others in highlighting the severity—and ongoing nature—of the latest attack:
The first is the continuing rise in the determination and sophistication of nation-state attacks. In the past week this has again burst into the headlines with the story of an attack on the firm FireEye using malware inserted into network management software provided to customers by the tech company SolarWinds. This has already led to subsequent news reports of penetration into multiple parts of the U.S. Government. We should all be prepared for stories about additional victims in the public sector and other enterprises and organizations. As FireEye CEO Kevin Mandia stated after disclosing the recent attack, “We are witnessing an attack by a nation with top-tier offensive capabilities.”
As Microsoft cybersecurity experts assist in the response, we have reached the same conclusion. The attack unfortunately represents a broad and successful espionage-based assault on both the confidential information of the U.S. Government and the tech tools used by firms to protect them. The attack is ongoing and is being actively investigated and addressed by cybersecurity teams in the public and private sectors, including Microsoft. As our teams act as first responders to these attacks, these ongoing investigations reveal an attack that is remarkable for its scope, sophistication and impact.
He assesses the breakdown of who was hit this way:
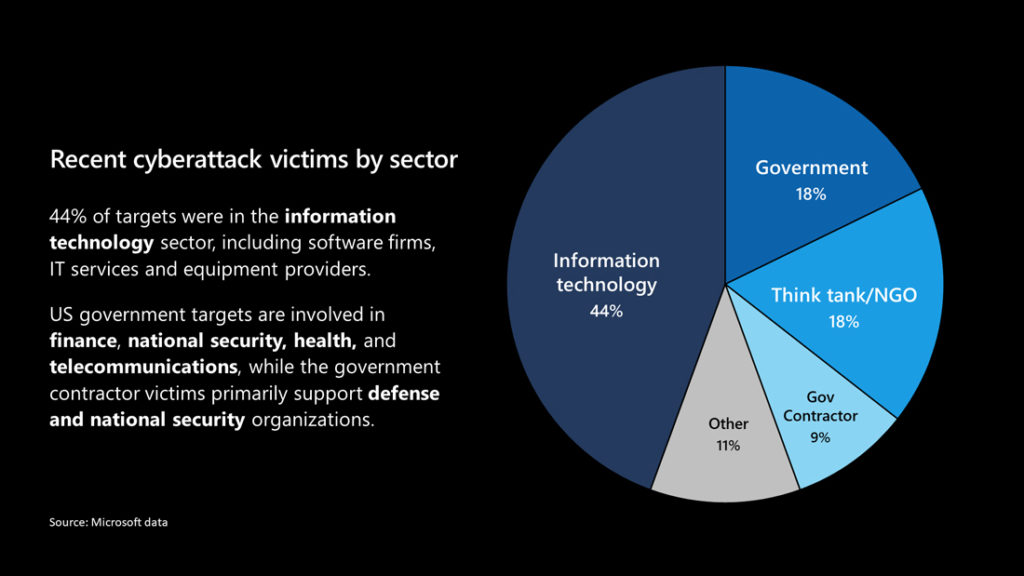
Additionally, he makes a strong claim that contradicts most of what I’ve seen from my national security types:
This is not “espionage as usual,” even in the digital age. Instead, it represents an act of recklessness that created a serious technological vulnerability for the United States and the world. In effect, this is not just an attack on specific targets, but on the trust and reliability of the world’s critical infrastructure in order to advance one nation’s intelligence agency. While the most recent attack appears to reflect a particular focus on the United States and many other democracies, it also provides a powerful reminder that people in virtually every country are at risk and need protection irrespective of the governments they live under.
Additionally, they’re more sophisticated that previous attacks:
These types of sophisticated nation-state attacks are increasingly being compounded by another technology trend, which is the opportunity to augment human capabilities with artificial intelligence (AI). One of the more chilling developments this year has been what appears to be new steps to use AI to weaponize large stolen datasets about individuals and spread targeted disinformation using text messages and encrypted messaging apps. We should all assume that, like the sophisticated attacks from Russia, this too will become a permanent part of the threat landscape.
Further, while this capability has been limited to a handful of state actors, with Russia as the most malign (and presumptively behind this attack not only because of its characteristics but because they’ve been unhit),
All this is changing because of a second evolving threat, namely the growing privatization of cybersecurity attacks through a new generation of private companies, akin to 21st-century mercenaries. This phenomenon has reached the point where it has acquired its own acronym – PSOAs, for private sector offensive actors. Unfortunately, this is not an acronym that will make the world a better place.
[…]
This represents a growing option for nation-states to either build or buy the tools needed for sophisticated cyberattacks. And if there has been one constant in the world of software over the past five decades, it is that money is always more plentiful than talent. An industry segment that aids offensive cyberattacks spells bad news on two fronts. First, it adds even more capability to the leading nation-state attackers, and second, it generates cyberattack proliferation to other governments that have the money but not the people to create their own weapons. In short, it adds another significant element to the cybersecurity threat landscape.
Not surprisingly, he wants united action against this set of threats:
Put simply, we need a more effective national and global strategy to protect against cyberattacks. It will need multiple parts, but perhaps most important, it must start with the recognition that governments and the tech sector will need to act together.
The new year creates an opportunity to turn a page on recent American unilateralism and focus on the collective action that is indispensable to cybersecurity protection. The United States did not win World War II, the Cold War or even its own independence by fighting alone. In a world where authoritarian countries are launching cyberattacks against the world’s democracies, it is more important than ever for democratic governments to work together – sharing information and best practices, and coordinating not just on cybersecurity protection but on defensive measures and responses.
Unlike attacks from the past, cybersecurity threats also require a unique level of collaboration between the public and private sectors. Today’s technology infrastructure, from data centers to fiberoptic cables, is most often owned and operated by private companies. These represent not only much of the infrastructure that needs to be secured but the surface area where new cyberattacks typically are first spotted. For this reason, effective cyber-defense requires not just a coalition of the world’s democracies, but a coalition with leading tech companies.
People like my old Atlantic Council colleague Jason Healy have been talking about the need for public-private partnership in this area for more than a decade. But, as I’ve noted before, the tech sector is inherently wary of the US government and tends not to see it as an inherently better actor than our autocratic competitors. At the governmental level, there is already considerable cooperation with our NATO allies, the EU, and the Five Eyes but I don’t claim to understand the extent or the gaps. But, rather obviously, the more cooperation there is, the more transparency that’s required and the more vulnerability that is created.
Smith closes with several paragraphs calling for specific actions that the incoming administration should take. Critiquing it is well beyond my expertise. But, rather obviously, the offense is ahead of the defense again in the cyber realm. And what we’ve done so far to punish Russia, China, North Korea and other malign actors has been inadequate to deter them.






Trump isn’t going to take this seriously for two reasons. The first is that he’s on his way out, and either wants to leave a lot of wreckage in his wake (for revenge against the country that rejected him) or he simply doesn’t care. The second reason is that he probably thinks this is no big deal: He himself doesn’t use computers (I remain surprised that he can operate a smart phone to Tweet) and doesn’t understand how they work or how significant this is. It’s outside his bubble. Therefore, it’s not important.
@CSK:
Russian puts bounties on US soldiers, Trump does nothing. Russia hacks US and other’s data networks, Trump does nothing.
You’re forgetting an incentive for Trump, he owes the Russians billions and he fears they will want to collect. He’s a traitor.
@Sleeping Dog:
Yes. Of course. Thanks for the reminder. I haven’t had coffee yet.
There is no way for a simple moke to know but one supposes that the ‘Five Eyes’ network has also been entered and exposed. We will be lucky to have anyone trusting us after this disaster.
What a chapter the Trump administration will have in our grandchildrens’ history texts!
BTW if anyone want to immediately increase their IQ on cyber security–this is your guy
https://www.schneier.com/
Been reading his blog off and on for 20+ years to supplement my own expertise–no one in the cyber security business can know everything about the subject. Bruce comes close.
One, I’m surprised neither Trump nor his cultists, enablers, backers, etc. are trumpeting this as proof the election was not secure at all and should be tossed and decided by the House.
Two, I’m sure the GOP leadership is working around the clock on this problem. It is their number one priority bar none: how to put the blame for this disaster on Joe Biden.
Trump cam in with Russia attacking our Democracy, nd he exits with Russia attacking our Government Agencies and technology infrastructure.
And in between he killed ~225,000 Americans through his incompetence.
That’s all I’ve got.
@JohnMcC:
That a hack happened, could have occurred in any administration, the crime here is that Trump and his sycophants, Pompeo and others are ignoring and denying that it was perpetrated by the Russian government. At best they are fools at worst they are complicit after the fact and maybe prior.
@Kathy:
No Obama.
@Jim Brown 32: Bruce really changed my way of thinking on something a few years ago. He said that with computer passwords, the smart thing to do is write them all down on a piece of paper and keep them in your wallet. That way you can come up with more elaborate passwords than you can remember, with a low security risk. Because you’ve got a proven track record of keeping your wallet secure, and the Ukrainian hackers you should be worried about can’t get your wallet.
@Daryl and his brother Darryl: 225,000 deaths was by mid-October. We’re well over 300k by now.
@JohnMcC: “There is no way for a simple moke to know but one supposes that the ‘Five Eyes’ network has also been entered and exposed. We will be lucky to have anyone trusting us after this disaster.”
That’s an excellent point! If Russian intelligence was roaming many thousands of government/contractor networks, then at the very least they’ve got a cornucopia of chunks of goodies. Where ‘chunk’ means ‘lists of what contacts what and when’ all the way up to ‘entire databases’.
I’ve worked on large software releases in a company that size. It’s plausible that you could find a place in the source to insert your hacks, but the level of observation and patience required to do it without getting noticed is impressive. Because anyone looking at the code is going to notice. But there are often stuff that’s established and working and nobody looks at, because they are busy doing other stuff in a code base that can be 10 million lines or more.
But still, you have to not break any build, or make notable changes to performance or to the size of exported binaries. It’s plausible that you suck down part or all of the source tree so you can do a build yourself just to make sure your changes don’t break anything.
There’s a level of patience and skill here that’s really impressive.
Trump approved of and benefited from the earlier Russian hacking and disinformation attacks. We did nothing. So the Russians persisted. And Trump will do nothing. Because, and I really can’t believe there’s anyone so dense they don’t know this by now: Trump is effectively a Russian asset.
The likelihood is that we’ve known about this for a long time but it was covered up by Trump’s loyal subjects. It’s only coming out now because Trump lost.
You know, as I said four years ago because it was bleedingly obvious then and even more obvious now. And yet, we still have chin-stroking contemplation of why we let this happen. Hmmm. Can’t quite figure it out.
I have difficulty imagining something that could deter them, them being hackers. But speaking probably for the majority who have ever been hacked, I would like all Super Bowl half-time shows to be centered around a hacker (chosen at random, any hacker will do) being slowly lowered feet first into a tank of piranha while either a marching band plays “Pop Goes The Weasel” or AC/DC plays “Hells Bells”, depending on the budget available.
This may only deter a few, maybe one one or two, I am aware of that. However we must not allow perfection to be the enemy of good!
And by a strange, strange coincidence, transition briefings by the Pentagon have been suspended for the next two weeks. I’m sure there’s nothing to see here. It’s totally because of the holidays. I’m sure someone will speak up with lots of examples of this happening during previous transitions.
A Tweet from Donnie on July 9, 2017…
This guy got played by so many people in so many ways. Kim used Trump like a hobby horse. But Putin, especially, played him like a fuqing piano.
I posted a substantial comment on this…but it didn’t appear. Now Im too lazy to retype. The TL/DR:
This is not a new frontier in hacking…it has long been known that Net management software and anti-virus software are great places to stages attacks. It is doubtful that the attack was sophisticated…if you probe long enough you’ll find a sys admin that simply makes a mistake and leaves a door unlocked.
The very structure of the internet and the centralization of IT services makes hacks like this possible. This is just the latest Salvo in a never ending game of espionage via cyberspace. Anything connected to the internet can be hacked given, time, resources, and will. Deterrence is a fallacy because of the low cost of entry into the tradecraft. The cost of this compromise to Russia was far less than the price of an M1 Tank. A cyber response is simply not punitive enough to force a recalculation and is expected anyway. Why do you think we have the best Intelligence apparatus in the world?
It is unlikely that our classified operational networks were compromised or you wouldn’t have heard about this compromise. Everyone breathe.. this is dog bites cat.
@Teve: Yes, password cracking dictionaries are now pretty state of the art and include finger-walking patterns. Its not a matter of if but when. You can add in a little extra complexity if you opt for multifactor authentication for your most sensitive accounts.
@Jim Brown 32:
I think this is more like Pearl Harbor, but we’re reassuring ourselves that they only got the battleships and the carriers are safe.
@Jim Brown 32:
A cyber response is simply not punitive enough to force a recalculation and is expected anyway.
On this, I agree. We should give the Ukrainians every weapons system they ask for. We should redouble sanctions and lean hard on the Germans to stop buying Russian gas. And, if there’s a way to do it without leaving too many fingerprints, a Russian sub should go to the bottom.
Here is the FireEyes report: Highly Evasive Attacker Leverages SolarWinds Supply Chain to Compromise Multiple Global Victims With SUNBURST Backdoor
This is a more extensive compromise than we’ve seen at any point previously, both in extent and in depth, and was the result of years of development by a nation-state actor. You don’t get the stuff this does on the cheap. It takes considerable knowledge, skill, and money.
And what’s worse is not only are they still in these networks, we have no idea what they took out or what they put in. You don’t spend the time and money it took to build this without making sure it persists.
@Michael Reynolds: Thats not to say there isnt valuable data to be gained from unclassified networks. There is. But being that Ive cashed checks for my opinions and recommendations in this area, there are scarier scenarios that I don’t want to put out into the ether. Once I saw that Bruce wasn’t all that alarmed either (and he has better placed sources than I do) it confirmed my gut instincts. The PH analogy is correct from the standpoint that our Adversaries are far more vested in cyber warfare than we are like Japan was actively fighting war when they decided to tangle with the US.
Right now we view cyber warfare as a niche irregular warfare component and the Big 4 adversaries basically have made it part of regular warfare doctrine. They’ve invested in the cyber equivalent of AK 47s and grenades and we are still at the level of limited use ballistic missiles.
@Jim Brown 32: you can make passwords too difficult to be worth cracking. 8WQW_|~+D,$CyfzL8^ Isn’t going to be cracked anytime soon. But if it’s my NYT or Slashdot password I’m not going to bother making it hard.
@Jim Brown 32: what do you think of 2FA?
@Teve:
So…Trump wants to guard election hacking???? Guard it? Does he mean guard it so no one will stop it?
@Jim Brown 32:
I’d be less concerned if I had any confidence that contractors etc… are hewing strictly to security protocols, but I am willing to bet that all sorts of damaging technical data has been firing back and forth on simple emails and texts.
And I’d be less concerned if I were not acutely aware of how weak people are, because I would also bet that compromising information re: sexual affairs and stock market insider profits involving anyone from low level clerks to US Senators are likely exposed to the Russians. And it’s painfully clear that a date with a rent boy, an unpaid debt, or a dirty stock trade are all it takes to get a Republican to sell out his country.
With nothing but flight schedules and emails to spouses the Russians can identify a courier carrying classified information. Or out an intelligence asset. Or identify a foreign government doing deals they shouldn’t be doing. Or discover a satellite that’s temporarily down. Or, or, or…
Thank God the Russians are fundamentally weak. But of course we have other enemies who the Russians can use against us with the right info.
@Teve: Raises the bar of entry of a target to AAA and Major Leagues hackers because you have to harvest 2 sets of credentials to present during the authentication session.
You have to be more patient and rely on some human error to get exploit this method. Most hackers are looking for low hanging fruit so, unless you specifically are being targeted 2FA/MFA moves you up a level on the tree.
If you are being targeted by pros….its only a matter of time and how bad they want access.
The exploitable flaw in rational people is lack of imagination. Right after 911 calls went out to creatives to produce scenarios because of course no sensible person had considered that you could fly a passenger jet into a skyscraper. Years earlier I’d started work on (and later abandoned) a novel predicated on the idea that you could flood the sub levels of a skyscraper with natural gas and spark it up – an extrapolation of the first WTC attack. (It’s a bit complicated but do-able.) Cooking up improbable scenarios – 911, underwear bombs, buying a game show host who’d later become president – is not the forte of intelligence analysts.
@Michael Reynolds: “The exploitable flaw in rational people is lack of imagination. Right after 911 calls went out to creatives to produce scenarios because of course no sensible person had considered that you could fly a passenger jet into a skyscraper.”
In 1996 my then-partner and I wrote a superhero pilot for Stan Lee and CBS in which the cultish bad guys brainwash (I think) the pilots of a jet to fly it into a skyscraper. Since that never got shot, we repurposed the idea for the season (and, as it turned out, series) finale of Martial Law on CBS. Which aired in May 2000. Two years later when Condoleeze Rice was running around saying “no one could ever have imagined such a thing,” I wanted to throw a TV at her.
@Sleeping Dog: but hey, a Biden staffer called Republicans’ f*ckers! That’s the real scandal!
@Monala: Next thing you know Biden will wear a tan suit.
@Daryl and his brother Darryl:
The next time a lizardoid runs for president, could they at least have the common courtesy to find one capable of pretending that English is their native language?
@wr: In the 1994 Tom Clancy novel debt of honor, a terrorist flies a 747 into the US Capitol building.
Holy cow Ali Velshi is going on Parler and trolling the Christianists.
https://twitter.com/oneunderscore__/status/1340081235792699394?s=21
Awesome
Speaking of Parler, a bunch of my Trumpy Facebook friends that made a big, dramatic Facebook exit for Parler and went as far as deleting their Facebook pages are suddenly creating new Facebook profiles. I guess it was just a dab too swampy, even for them. 🙂
@Monala:
You have a point, I need to keep things in perspective.
@Jax: Parler made the mistake of saying they don’t do any censorship, so the neo-Nazis and perverts went there and started posting kill the jew stuff and dick pics etc and now they’re banning people too.
@Teve:
In one of Adam Hall’s* “Quiller” novels from the 70s, terrorists take over a commercial jetliner, fill it with nerve gas, and aim for the White House.
*The name Elleston Trevor used to write that particular series. Still my favorite spy novel series of all time.
@wr:
In 1994, Algerian terrorists hijacked an Air France A300 with the intention of crashing it into, or blowing it up over, the Eiffel Tower. French comandos liberated the plane and killed the hijackers when the plane stopped in Marseilles.
So, in a way it had already been attempted.
Well, the Japanese imagined it well before Tom Clancy did.
There was a bit if a problem facing any imaginative cop: The existing and internationally accepted policy for hijacks, based on many incidences of Palestinians and misc. nut jobs, was cooperate and nail them after they got on the ground. It has to be considered that changing that policy radically prior to 9/11 would have been a heavy, heavy lift.
@dazedandconfused: coincidentally, in Debt of Honor the guy who flew the 747 into the Capitol was Japanese. 😮